A more recent example of spear-phishing that seems to have recirculated in the community takes advantage of the trust set up for Google links. The exploit takes advantages of the fact that the phishing links set up in a Google comment bypass email monitoring and phishing URL protection.
The attack starts with setting up a document within Google’s workspace suite, such as Documents or Slides, and invite the target to spear-phish into the document by using the @ function in the comments section. This invite will send a notification email to the target’s inbox, and since the email comes from Google’s servers, it won’t be filtered by email security (Microsoft ATP doesn’t detect this either).
Only the display name is shown in the notification email and not the attacker’s email address. This means that the target can be exposed very easily by impersonating as a colleague or friend sending a link
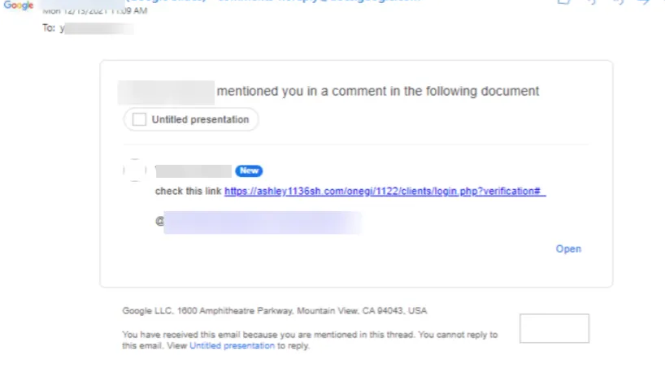
Google Slide example. Source: https://www.itpro.co.uk/software/google-docs/361922/researchers-spot-spear-phishing-exploit-in-google-docs
It preys on trust and overconfidence in URL scanners to detect phishing. This vulnerability has yet to be addressed as the emails come directly from Google’s email servers. Anyone can create a random gmail account and create a document. The notification email becomes the payload as the email doesn’t give an option for the victim to view the document itself, just the comment that was made.
To protect yourself from this, you’ll have to keep an eye out for grammar, links, double confirm with the sender (usually best through another source other than the potential attack vector, in this case email, i.e. call them). A hard line measure off the top of my head for an enterprise is to create a policy with fine-tuned trigger alerts and URL blocking. Not sure how well it can be implemented but it could be investigated…
Dictionary triggers: Google, comment, mentioned
Domain: *.google.com (e.g. mail.google.com, docs.google.com)
Block URLs
At the very least, the emails will get flagged (more effective if the organisation doesn’t use Google Workspace), prevent users from immediately clicking the links, and it will give them a moment to think about it before proceeding.
From Google’s end, they can just as easily include email addresses along with the name in the comment. It will allow victims full visibility of the email and domain. Or, disable the ability to @ an email in the comments and only allow comments to @ a person if the document is shared and accepted by them.
So what does it look like in practice?
As an experiment, I decided to impersonate a Director at UNSW to spear phish a facilitator using strong wording. I was given prior consent, which increased the difficulty.
My goal: To create panic and assign fault, creating a believable urgency that requires the target to click on the link.
Setting up the URL
As most of these exercises would suggest, obfuscation and separation of yourself from the constructed identity is key. Usually a domain with a legitimate looking name would be purchased for nefarious means, such as phishing in this instance.
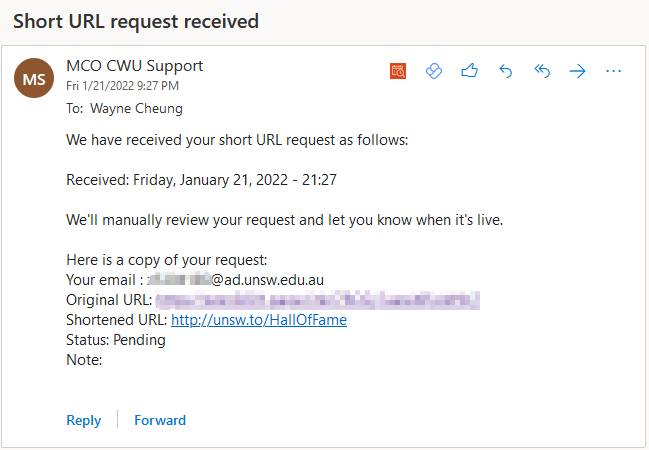
I didn’t want to purchase a domain. Rather, I looked into shortening the ‘malicious’ link (it wasn’t. Just a rick roll) into a believable URL. At first, I tried to create a legitimate shortened URL using UNSW’s own URL shortener system, however it required a manual verification process. In hindsight, this is a dangerous precedent for an attacker as it could trigger an alert in their system and admins would be notified and alarmed by this.
In the end, I resorted to bit.ly and renamed the URL to reflect a fake log generated by an ‘automated alert system’ that detects plagiarism or other misdemeanors.
Setting up the Google document
The Gmail email account name doesn’t matter. Only your name is shown, and not the email.
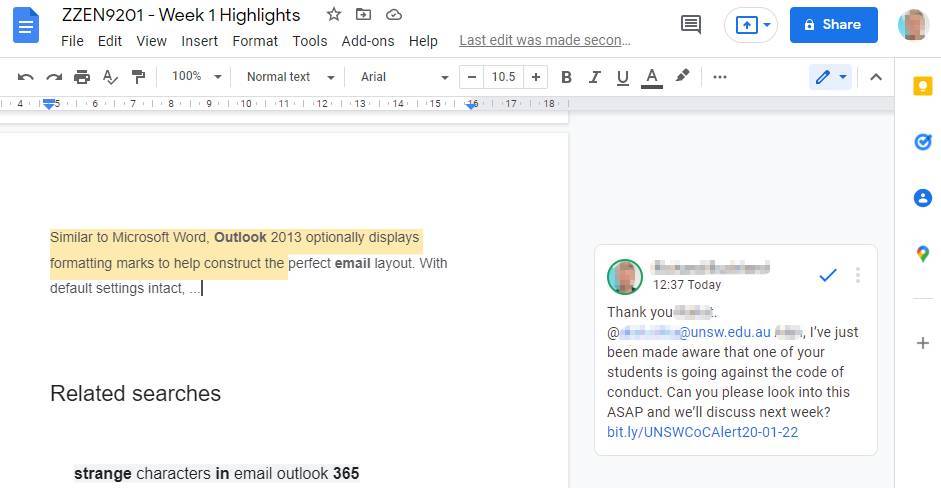
The contents of the document are irrelevant, however after testing and setting up multiple fake accounts, your document requires legitimacy and must have content inside. Google flags your account for authenticity and detects violations of terms of service. Based on an initial observation, it checks for suspicious behaviour such as:
New account > new document > share immediately
To bypass this, you can simply go through the motions of a ‘normal user’ to give it more authenticity, such as adding a profile photo and following through the recommended Gmail steps for account setup. Failure to do this will result in email notifications never making it to the target email address. This was found after multiple tests and receiving an email notification for suspicious activity around 30 minutes later, resulting in having to create another account.
Establishing the comment
Comments are restricted in length before the comment suffers from content overflow, so it is required to keep the commenting concise. I experimented with the length of comment whilst taking into consideration mannerisms of the person’s writing through existing articles and speech pattern in podcasts. Some iterations of comments include:
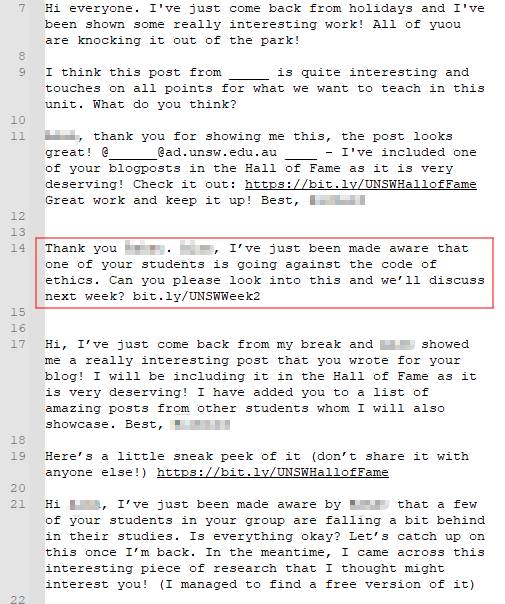
The final result
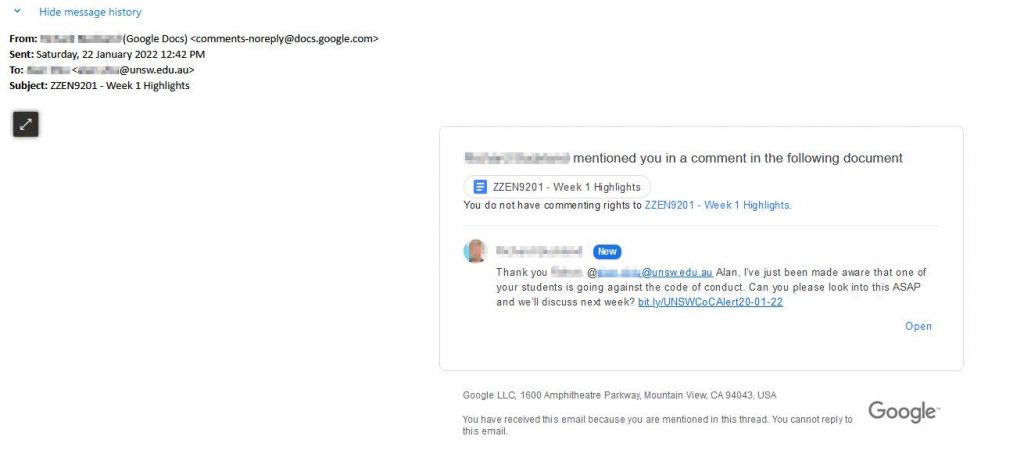
Was I successful? Who knows. Maybe setting up a listener could be a future project.
Additional readings for that then:
https://www.sciencedirect.com/topics/computer-science/spear-phishing-attack
