Deepwater Horizon reflects an ongoing issue in cybersecurity, in that panic and urgency disrupts protocols and throws the manual out the door in the face of desperation. To reflect on this incident, here are proposed recommendations I suggest that revolve largely around preventative measures.
- Overview and assessment pertaining to the regulations of oil rigging.
- An independent body like the ASIC, EPA etc.
- Independent certifier or inspector conducting regular visits for audit.
- A bond to be drawn down on, where the companies involved are required to chip in to ensure some form of commitment to the project
- Review into fail-safe designs that incorporate various techniques to mitigate losses due to system or component failures
Valid points can be raised against establishing an independent body, such as the red tape involved, where the responsibility would lie, and the bureaucracy of establishing a governing body. There are fine complexities involved in each argument, however I argue that:
- Whilst red taping (saying no and restrictions involved) is considered negative and limits the movement and activities of companies willing to establish deep sea oil rigs, there is also a positive spin on it. Regulating the design, checking against codes and auditing the oil rig before deployment allows for an established set of safety controls to be implemented whilst urging companies to conduct safe and industry work practices. Cybersecurity should never be about red tape (as I highlighted in the discussion). We are a force of good for the company to make sure what they decide to do does not threaten the safety or expose vulnerabilities within the business. Rather, it is about compromise and allowing their existence to flourish while making sure oil rigs are up to code and does not threaten the safety of others, whether it is the workforce, equipment or environment.
- Independent certifiers are prevalent in various industries where there are major risks inherent in large scale ventures, especially when dealing with complex systems. Establishing these certifiers can be seen as a benefit to review design, operations, maintenance, safety and provide recommendations for review before giving the green light. This is much like how cybersecurity experts become industry certified to verify their capability.
- Whilst bureaucracy is inherent in all governing bodies and is seen as a thorn in the backside, they are necessary to keep authorities in check (just take the ICAC for example). Large projects are met with resistance however with a sensible approach, it is possible to get authorities on board with the idea. Cybersecurity isn’t always about defense, but also about telling management why security is a good thing, why it is needed in areas of the business, and how it benefits the business. Resistance isn’t just from the adversaries, but also from upper management.
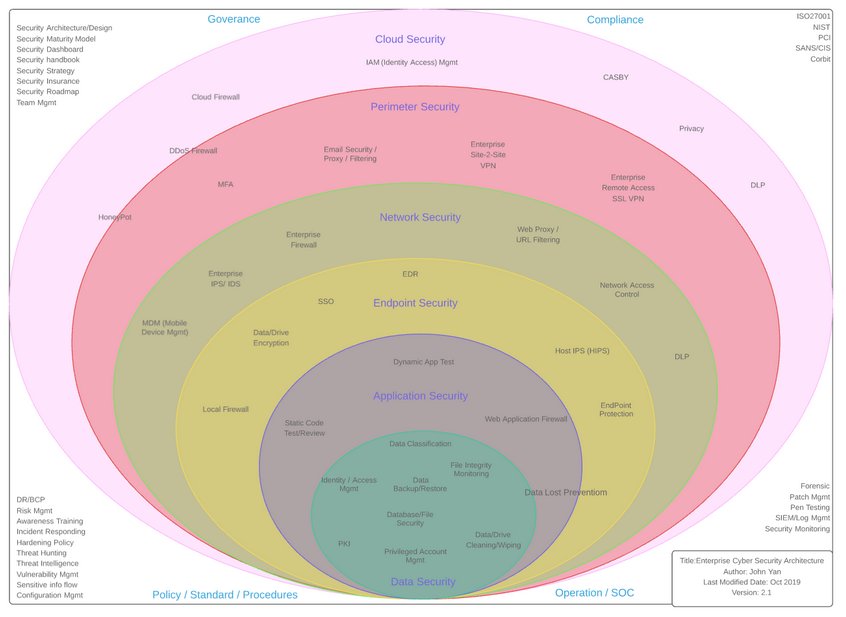
Personally, fail-safes are a no brainer for reinforcing defense to prevent incidents. You have layers and layers within your defense to protect yourself in case one part of the chain is broken into. Think of firewalls. You have external firewalls protecting your enterprise from intruders, while the internal firewall protects your network from attacks that have broken past the first (external) firewall.
However, we can also bolster this notion of multiple defense by considering lateral and complementary defense within each layer to support the perimeter.