Making Phishing Campaigns easier OpenAI’s release of the new ChatGPT bot has been a hot bed of excitement for automated…
DUCTF DFIR Shop Challenge Write-Up
A complete write-up for the DUCTF DFIR challenge investigating logs of a shop’s website.
Securing Active Directory
Securing Active Directory (AD) is an important aspect of cybersecurity for any enterprise using it. AD is a central piece…
Predictive Analysis of Employing and Crowdsourcing Hacker Groups
Overview Current trends seemingly indicate Russia is amid conducting damage and media control, psychological attacks, disrupting public order and pushing…
Timeline of Cyber Incidents Attributed to the Russian-Ukraine Conflict
Disinformation, false flags, DDoS attacks, and destructive wiper malware are a part of Russian military doctrine.” Rick Holland, Digital Shadows…
Zero-Risk Bias
Zero-risk bias is a flawed concept in cybersecurity. Absolute security with no vulnerabilities or weaknesses is a pipe dream that…
Experimenting with the Google Comment Exploit
A more recent example of spear-phishing that seems to have recirculated in the community takes advantage of the trust set…
Stuxnet Worm and the Iranian Nuclear Program
The Stuxnet worm has been significantly flogged and for good reason. It is a great historical example that can teach…
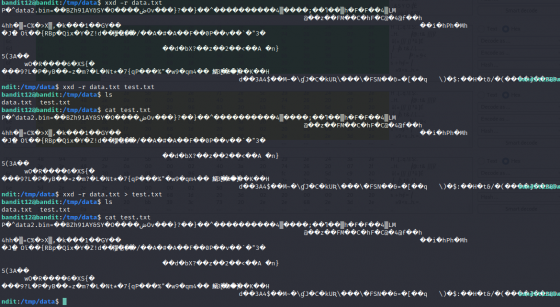
Over The Wire: Bandit Level 12
This one took a bit more out of me at the start as I was fumbling around trying to convert…
Blackmatter ransomware: a super broad overview
I’d like to write about this activity from a broader view of an attack. This is because analysing any attack…
Case study of Deepwater Horizon incident and its relation to cybersecurity
Deepwater Horizon reflects an ongoing issue in cybersecurity, in that panic and urgency disrupts protocols and throws the manual out…
Where is the cybersecurity audit policy?
Earlier this week, I came across a random thought which puzzled me. A significant number of Australian businesses, by law,…
Mimecast x CrowdStrike webinar summary
I sat in a Mimecast x CrowdStrike webinar where they briefly touched on the threat landscape and how ransomware is…
30 minute research: Hypothetical NSW Tsunami Disaster
A hypothetical volcano eruption will require an evacuation as the NSW Government (SES more likely) has issued an alert for…
Installing pfSense via Hyper-V [in progress]
This project is ongoing and a complement to my other current project of securing a Raspberry Pi (or any other…
Securing a Raspberry Pi with best practices
Update 20/7/21 Originally installing Crowdstrike was included in this project, but I had a good chat with cybersec and was…









![Installing pfSense via Hyper-V [in progress]](https://i0.wp.com/waynecheung.com.au/wp-content/uploads/2021/07/diagram-1.png?resize=560%2C9999&ssl=1)